GEM-2 Programmable Cryptographic Module
Key Features
■Compatible with many cryptographic algorithm ■Easy key management ■High speed data rate up to 300Mbps ■FPGA/CPLD ■Full compatible with Glocom products
Target Applications
■All GR-Series Radios (e.g. Handheld, Man-pack, Vehicular, or Station Radio) ■Handheld & Mobile Law Enforcement (battery-powered) radios ■Telemetry and military sensor systems ■Network interface cards and IP security products ■Secure Wireless Networks ■Homeland Security applications ■Next Generation Key Management Modules
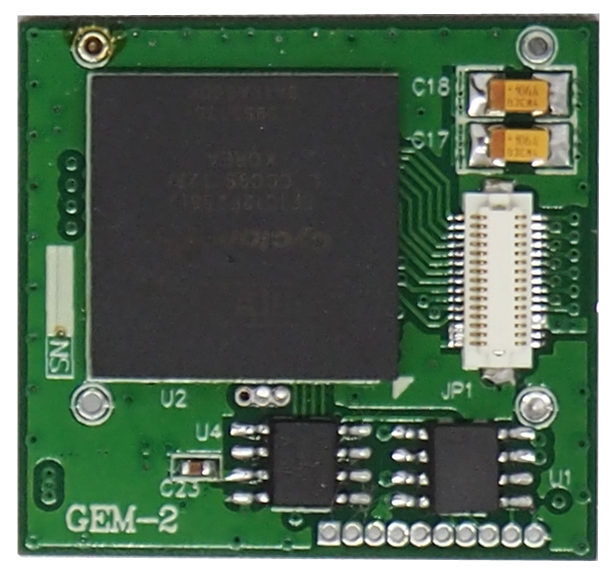
Encryption Module
GEM-2 consists of a miniaturized printed wiring assembly, custom Application Specific Integrated Circuit (ASIC) and supporting software that is embedded in radios and other voice and data communications equipment to encrypt classified information prior to transmission and storage. GEM-2 is the second product in Glocom encryption family supporting all of the features of GEM-1. GEM-1 was installed on the DSP module in radio systems. GEM-2 encompasses a much broader range of functionality and offers data rates greater than 300 Mbps, low power consumption suitable for mobile (battery powered) applications, legacy and future algorithm support and advanced programmability. GEM-2 was developed by Glocom to meet all of the requirements of the Joint Tactical Radio Systems (JTRS) and other military or para-military communication , including the requirement for programmability. GEM-2’ software programmability provides a low cost migration path for future upgrades to embedded communications equipment without the logistics and cost burden normally associated with upgrading hardware. GEM-2’s small size, low power and high data rates make it an ideal choice for mobile (battery powered) applications. It is ideally suited for JTRS applications, military radios, wireless LAN’s remote control/remote sense/telemetry, guided munitions, UAV, USVs and other equipment requiring a low power, programmable solution.
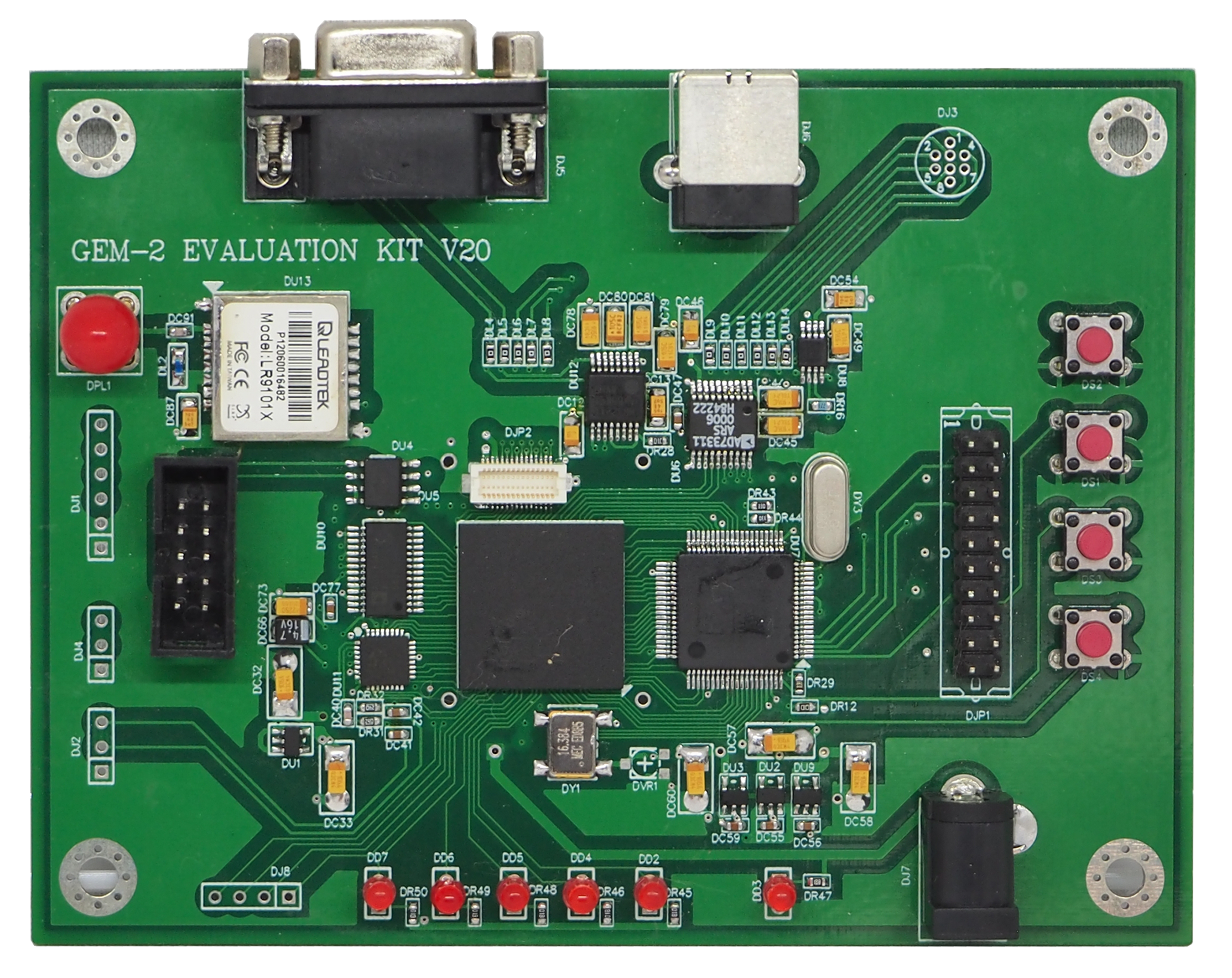
Evaluation Kit V20
Kit includes:
■Evaluation board ■User’s Guide and Encryption Module documentation ■Encryption Module Terminal Program ■Evaluation kit software with GUI interface for entering commands and traffic ■5V AC adapter
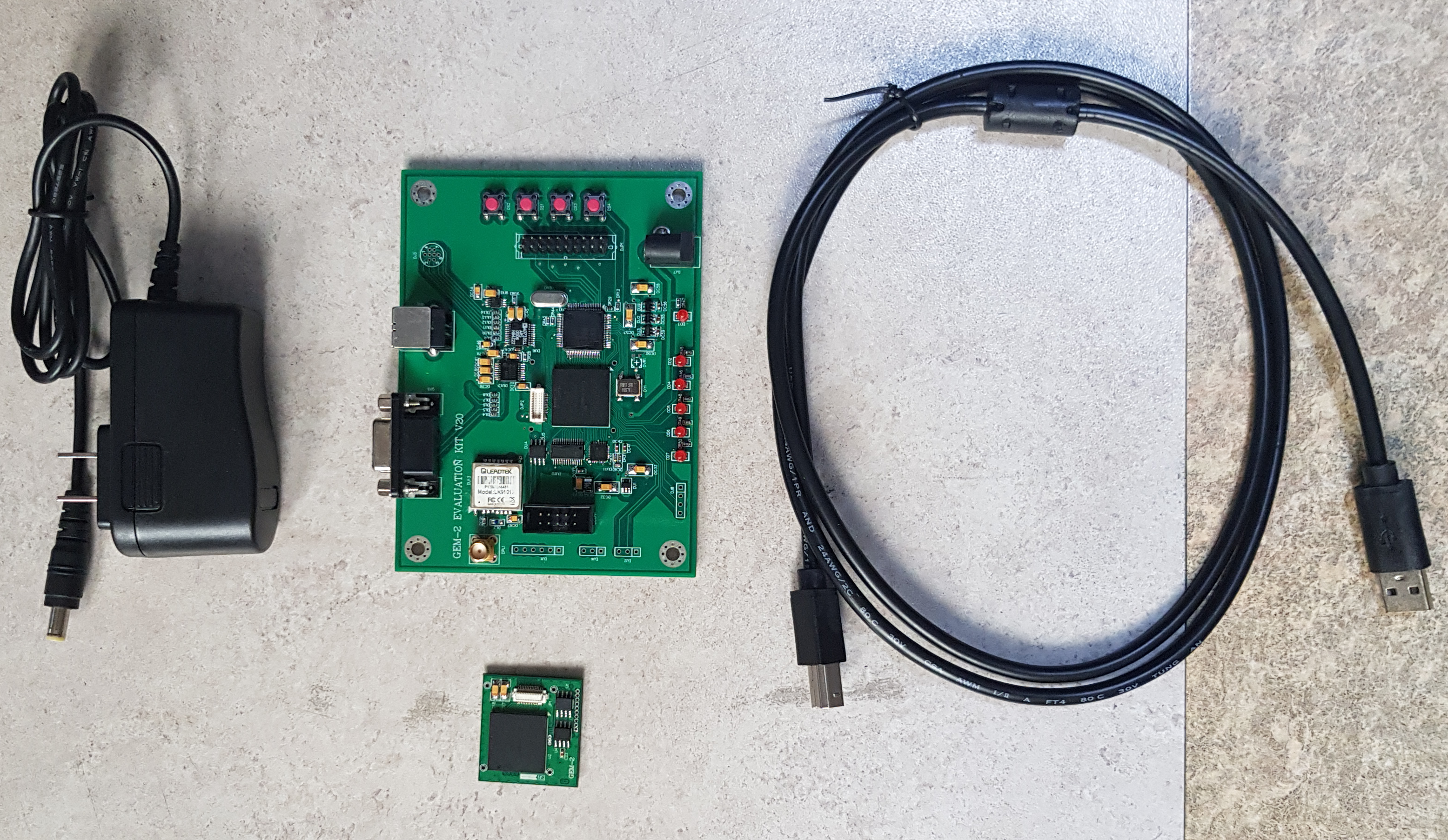
GEM-2 Set